Indeed, it is very important to raise your security posture with AWS infrastructure and services. With the most versatile and secure Application AWS cloud computing environment available today, AWS gives you the power and trust you need to operate your business safely. As an AWS client, you will have access to AWS data centers and a network designed to safeguard your data, identities, applications, and devices. With AWS’s broad services and capabilities, you may increase; your ability to satisfy fundamental security and compliance needs such as data location; protection, and confidentiality.
AWS enables you to automate tedious security activities, allowing you to focus on developing and innovating your organization. Furthermore, you only pay for the services that you utilize. AWS is the only commercial cloud that has had its service offerings and related supply chain evaluated and accepted as safe enough for top-secret workloads, which benefits all customers.
Top 6 Benefits of Security Application on AWS Cloud
AWS first focus is security, and AWS has robust security tools to safeguard practically any workload. They provide possibilities to secure your data, monitor security-related behavior and get automatic replies through AWS Security services. This enables our clients to improve their cloud security posture, offer more flexible IT, and save expenses. With that in mind, consider the following; six benefits of cloud security.
1. Compliance and Security Integration
You may use AWS activity monitoring services to identify configuration changes and security incidents; as well as integrate AWS activity with your existing monitoring systems; for simpler compliance reporting. We deliver compliance reports based on managing hundreds of security controls inherited across the AWS platform, making meeting security and compliance standards easier and faster.
2. Cloud Computing, Large data, and Security

Our clients utilize the cloud to protect the cloud because it gives low-cost access to vast amounts of; storage and processing resources (they run big data analytics on security data and log data, which provides more insight into their security posture and results in much faster remediation of issues). Use the cloud’s storage and processing capacity to locate security incident needles in a haystack.
3. Visibility, Uniformity, and Automation
The cloud allows you to select from a diverse, but a more homogenous collection of infrastructure and capabilities. What should be utilized in your environment may be controlled down to the operating system image level. Your security specialists may evaluate a predefined configuration of systems using cloud orchestration; tools like Application AWS Cloud Formation, and then those can be “stamped out” with all security measures activated and in place. You may, for example; use AWS Quick Starts to automate the configuration of AWS resources to fulfill a variety of compliance needs.
4. Extensive Ecosystem of Security Partners & Solutions
Extend the benefits of AWS by utilizing security technologies and consulting services from well-known and trusted solution providers. We have carefully chosen suppliers with significant experience and shown performance in securing every stage of cloud adoption, from initial migration to continuing day-to-day administration.
5. System And Application Customer Focus
The cloud minimizes the overall “security surface area” that client security specialists must control. Because of our shared responsibility approach, you can concentrate your skills on higher-level operating systems and application security management. You maintain control over the security you choose to deploy to safeguard your own information, apps, systems, and networks, just as you would for on-premises data center applications.
6. System Containers

Cloud platforms are “systems containers” that surround existing systems and give more visibility into their behavior and functioning, including security vulnerabilities, resulting in a new type of “protection in depth.” The “container” that runs your operating systems and applications is software that is configurable, monitorable, and reactive. For example, without understanding anything about your application’s internal workings, you may establish monitoring alerts at the infrastructure level that will trigger a smart response to any odd activity.

The cloud narrative will only get better as innovation speeds up and scales up. AWS will continue to push the envelope in order to provide our clients with IT infrastructure and security services that are agile, visible, scalable, and secure. By providing safe, agile, and cost-effective IT services, we have earned the trust of government mission owners due to our track record of operational integrity and quick speed of innovation.
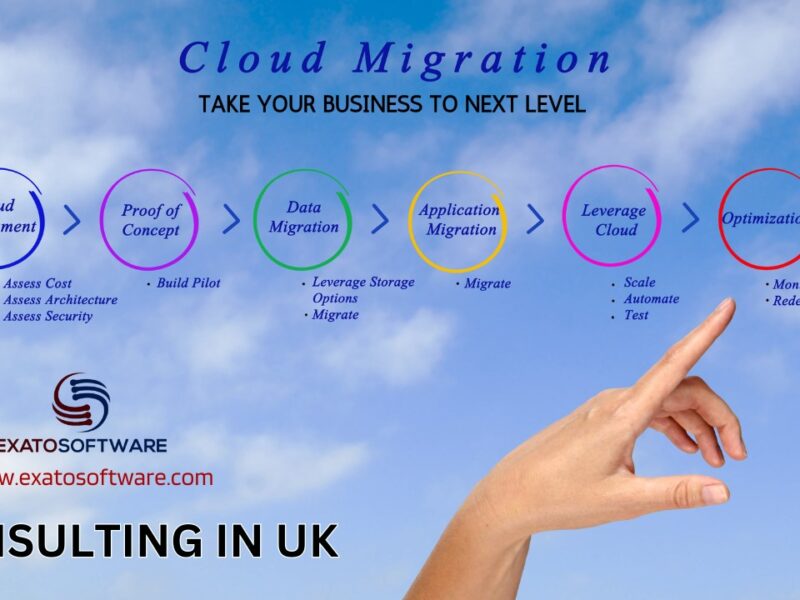
Achieve Application on AWS Cloud in 6 Steps
Indeed, it is even better to avoid committing; the mistake in the first place. Here’s a 10-step approach to understanding security best practices frameworks and how customers should best apply the AWS platform and its services.
1. Adhere to IAM Best Practices
- The AWS Identity and Access Management Service allow users to securely manage their access to AWS services and resources.
- The AWS account may be managed by creating groups and users and assigning granular permission restrictions to users to restrict access to APIs and resources. This video delves into IAM policy management.
- Follow the “least privileges” approach to security when providing IAM roles.
- Passwords and access keys should be rotated.
2. Maintain OS-level Access and the Security of Ec2 Instances
- Create an OS-level vulnerability report, and run an inspector evaluation.
- To maintain OS packages up to date, use System Patch Manager.
- Safeguard your infrastructure from newly identified defects and vulnerabilities, and patch the EC2 instance on a regular basis.
- Follow the security recommendations; supplied by operating system suppliers such as RedHat, Suse, and Microsoft. From a security standpoint, this helps to maintain all OS-specific programs up to date.
3. Encryption
- AWS offers two encryption methods: in transit and at rest.
- Use AWS KMS to store at-rest encryption keys, which can be produced by AWS or provided by the client.
- Utilize CloudHSM to supply hardware-encrypted devices for key storage. You may generate an SSL certificate for the public domain using AWS Certificate Manager.
- Most AWS services offer in-transit encryption via HTTPS endpoints that allow end-to-end encryption.
4. Network Safety
- Intrusion detection systems (IDS) and intrusion prevention systems (IPS) identify and prevent assaults on key infrastructures, such as payment gateways for banking-related transaction applications.
- To monitor network traffic, VPC flow logs should be enabled.
- Restriction of access based on security group (EC2, RDS, Elastic Cache, etc.)
- Use Guard Duty to continually monitor AWS accounts and infrastructures.
5. Security of Web Applications
- Deep packet inspection is provided by web application firewalls (WAF) for web traffic.
- In addition, WAF can aid in the prevention of platform and application-specific attacks, protocol sanity assaults, and unauthorized user access.
- Amazon Inspector is an automated security evaluation solution that enhances the security and compliance of AWS-hosted applications.
- Use AWS (Amazon Web Service) Cognito to securely authenticate application user pools. It also supports Google, Facebook, and Amazon federated access.
6. Follow the AWS Database and Storage Services Security Best Practices
- Restriction of RDS instance access reduces the risk of malicious activities such as brute force attacks, SQL injections, or DoS attacks.
- S3 storage should be encrypted in transit and at rest.
- To restrict access to S3 material, use S3 policy. If you don’t need to disclose items, keep your S3 bucket private.
- AWS (Amazon Web Service) Macie may be used to discover and safeguard sensitive data within AWS-S3.
- Use the AWS Parameter Store to store environment-specific credentials and secrets for your cloud-native application, which you can simply do utilizing secrets management.