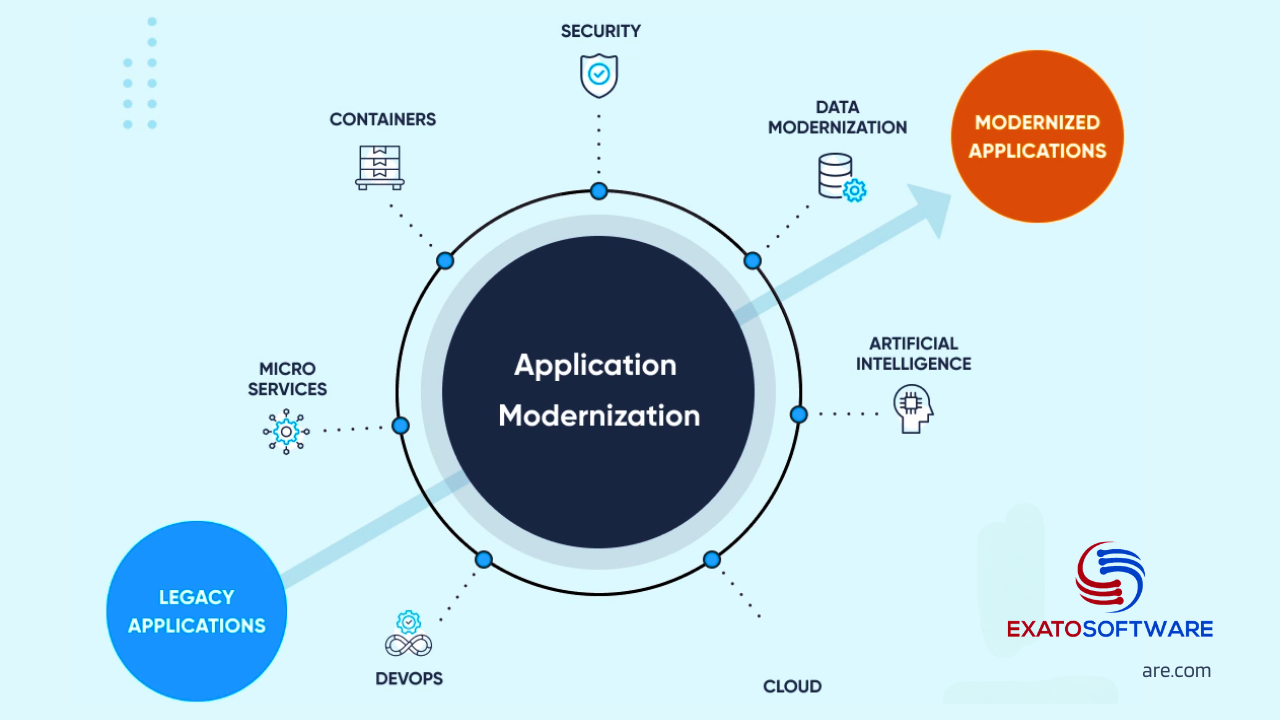
Modernizing a legacy .NET application involves updating its architecture, technologies, and processes to align with contemporary standards and improve its overall performance, scalability, maintainability, and user experience.
Evaluate and Assess the current Application
Evaluating a legacy application for transitioning involves a systematic approach to understand its architecture, codebase, dependencies, and business requirements. Here’s a step-by-step process to evaluate a legacy application for transitioning:
1. Understand the Business Context:
Identify Stakeholders: Determine the key stakeholders involved in the application, including business owners, developers, and end-users.
Gather Requirements: Understand the business goals, user needs, regulatory requirements, and any constraints that influence the transition process.
2. Document Current State:
Architecture Documentation: Review existing architecture diagrams, documentation, and system components to understand the application’s structure and dependencies.
Code Analysis: Perform a code review to assess the quality, complexity, and maintainability of the codebase. Identify technical debt, outdated libraries, and potential areas for improvement.
Dependency Mapping: Identify dependencies on external libraries, frameworks, databases, and third-party services.
3. Assess Technology Stack:
Framework and Language Versions: Identify the versions of .NET framework, programming languages (e.g., C#, VB.NET), and related technologies used in the application.
Compatibility Analysis: Evaluate compatibility with newer versions of .NET framework, operating systems, and third-party components.
Platform Support: Determine if the application is designed for on-premises deployment or if it can be migrated to cloud platforms.
4. Evaluate Scalability and Performance:
Scalability Analysis: Assess the application’s ability to handle increased loads, concurrent users, and data volume.
Performance Testing: Conduct performance tests to identify bottlenecks, latency issues, and areas for optimization.
Resource Utilization: Analyze resource usage patterns, such as CPU, memory, and disk I/O, to identify inefficiencies and optimize resource allocation.
5. Security and Compliance Assessment:
Security Audit: Review security controls, authentication mechanisms, authorization policies, and data encryption practices.
Compliance Check: Ensure compliance with industry standards (e.g., GDPR, HIPAA) and regulatory requirements specific to the application’s domain.
6. Data Migration and Management:
Data Analysis: Analyze the structure, volume, and relationships of data stored by the application.
Data Migration Strategy: Define a strategy for migrating data to modern databases, data lakes, or cloud storage solutions.
Data Cleansing and Transformation: Identify data quality issues and perform data cleansing, normalization, and transformation as needed.
7. Assess User Experience and Accessibility:
User Interface Evaluation: Evaluate the user interface design, navigation flow, and responsiveness across different devices and screen sizes.
Accessibility Compliance: Ensure compliance with accessibility standards (e.g., WCAG) to accommodate users with disabilities.
8. Risk Assessment and Mitigation:
Risk Identification: Identify risks associated with the transition process, such as data loss, downtime, compatibility issues, and user acceptance.
Risk Mitigation Plan: Develop a risk mitigation plan with strategies to address identified risks, allocate resources, and manage stakeholder expectations.
9. Cost-Benefit Analysis:
Cost Estimation: Estimate the costs associated with transitioning the application, including development efforts, infrastructure upgrades, licensing fees, and training.
Benefit Analysis: Evaluate the potential benefits of transitioning, such as improved performance, scalability, security, and compliance, against the costs incurred.
10. Develop Transition Roadmap:
Prioritize Initiatives: Prioritize transition initiatives based on business impact, technical feasibility, and resource availability.
Define Milestones: Define clear milestones, timelines, and deliverables for each phase of the transition process.
Engage Stakeholders: Collaborate with stakeholders to validate the transition roadmap, address concerns, and ensure alignment with business objectives.
Incremental Refactoring
Break Down Monoliths: Decompose monolithic applications into microservices to improve agility, scalability, and maintainability.
Breaking down a monolithic application involves decomposing it into smaller, more manageable components, often referred to as microservices, which are loosely coupled and independently deployable. Here are steps to break down a monolithic application:
1. Identify Bounded Contexts:
Analyze the functionality and domain model of the monolithic application to identify distinct areas of business logic and functionality, known as bounded contexts. Bounded contexts represent cohesive units of functionality within the application that can be logically separated and encapsulated.
2. Define Service Boundaries:
Once bounded contexts are identified, define service boundaries around each context, delineating the scope and responsibilities of individual microservices. Consider factors such as data ownership, transaction boundaries, and domain-driven design principles when defining service boundaries.
3. Decompose into Microservices:
Extract functionality from the monolithic application and encapsulate it within separate microservices based on the defined service boundaries. Each microservice should have a well-defined interface, exposing functionality through APIs, and encapsulating its own data storage and business logic.
4. Establish Communication Mechanisms:
Implement communication mechanisms between microservices to enable inter-service communication and coordination. Use lightweight protocols such as HTTP/REST, messaging queues, or event-driven architectures to facilitate communication between microservices.
5. Refactor Shared Components:
Identify shared components or modules within the monolithic application that are candidates for reuse across microservices. Refactor shared functionality into separate libraries or services that can be consumed by multiple microservices, promoting code reuse and maintainability. You can use dependency injection, Domain-Driven designs, and SOLID principles to refactor monolithic code to improve modularity, maintainability, testability, and alignment with business requirements.
a. Dependency Injection (DI)
Problem Addressed: Legacy applications often suffer from tight coupling between components, making it difficult to modify, test, and maintain the codebase.
Solution Provided: Dependency Injection decouples components by removing direct dependencies between them. Instead of creating dependencies internally, components rely on external dependencies provided to them.
Benefits in Refactoring
Loose Coupling: DI allows components to be loosely coupled, making it easier to replace or modify dependencies without impacting the rest of the system.
Testability: By injecting dependencies, components become easier to test in isolation, facilitating the adoption of automated unit testing and improving overall code quality.
Modifiability: DI promotes modular design and separation of concerns, enabling more flexible and maintainable code that can evolve over time.
b. SOLID Principles
Problem Addressed: Legacy codebases often violate the principles of good object-oriented design, leading to code that is rigid, fragile, and difficult to extend or refactor.
Solution Provided: The SOLID principles (Single Responsibility, Open/Closed, Liskov Substitution, Interface Segregation, Dependency Inversion) provide guidelines for designing maintainable and extensible software systems.
Benefits in Refactoring:
Single Responsibility Principle (SRP): Encourages the design of classes with a single, well-defined responsibility, reducing complexity and improving code maintainability.
Open/Closed Principle (OCP): Promotes extensible designs that allow new functionality to be added without modifying existing code, minimizing the risk of introducing regressions.
Liskov Substitution Principle (LSP): Ensures that derived types can be substituted for their base types without altering the correctness of the program, facilitating polymorphic behavior and code reuse.
Interface Segregation Principle (ISP): Advocates for small, cohesive interfaces tailored to the specific needs of clients, preventing clients from depending on unnecessary functionality.
Dependency Inversion Principle (DIP): Encourages the use of abstractions and interfaces to decouple high-level modules from low-level details, promoting flexibility and testability.
c. Domain-Driven Design (DDD)
Problem Addressed: Legacy applications often lack a clear understanding of the underlying domain, leading to misaligned designs, bloated models, and complex business logic.
Solution Provided: Domain-Driven Design emphasizes the collaborative exploration of complex domains between domain experts and software developers, focusing on modeling the domain using rich, expressive domain concepts.
Benefits in Refactoring:
Ubiquitous Language: DDD promotes the adoption of a shared, domain-specific language that aligns with the mental model of domain experts, fostering better communication and understanding between stakeholders.
Bounded Contexts: DDD encourages the identification of bounded contexts within the domain, allowing developers to define clear boundaries and models that reflect the specific contexts in which they operate.
Aggregate Roots: DDD introduces the concept of aggregate roots to enforce consistency and transactional boundaries within the domain model, guiding the design of cohesive, transactional units of work.
Strategic Design: DDD provides strategic design patterns and principles, such as bounded contexts, context mapping, and domain events, to guide the architectural decisions and organization of large-scale systems.
7. Implement Cross-Cutting Concerns:
Address cross-cutting concerns such as authentication, authorization, logging, and monitoring in a centralized and consistent manner across microservices. Consider using API gateways, service meshes, or centralized infrastructure components to manage cross-cutting concerns effectively.
8. Adopt DevOps Practices:
Implement DevOps practices such as continuous integration, continuous deployment, automated testing, and infrastructure as code to streamline the development, deployment, and operation of microservices.
9. Monitor and Manage Complexity:
Monitor the complexity and dependencies between microservices using tools and techniques such as service mesh, distributed tracing, and dependency analysis. Implement practices such as service versioning, circuit breakers, and fallback mechanisms to manage failures and ensure resilience in distributed systems.
10. Iterate and Refine:
Embrace an iterative approach to decomposing the monolithic application, prioritizing high-impact areas and addressing technical debt incrementally. Solicit feedback from stakeholders, monitor system performance, and adapt the architecture based on evolving requirements and lessons learned.
Containerization and Cloud Adoption
Containerize Applications: Package legacy applications into containers using Docker to improve portability, scalability, and deployment consistency.
Orchestrate with Kubernetes: Deploy and manage containerized applications with Kubernetes for automated scaling, monitoring, and resource optimization.
Migration to Cloud: Move applications to cloud platforms like Azure, AWS, or Google Cloud for improved scalability, reliability, and cost-efficiency.
Utilize Cloud Services: Leverage managed services like Azure App Service, AWS Lambda, or Google Cloud Functions for tasks such as hosting, authentication, and database management.
API-Driven Architectures
Expose APIs: Expose functionality through well-defined APIs to enable integration with other applications, services, and devices.
Implement RESTful Services: Design RESTful APIs for flexibility, simplicity, and interoperability with various client applications.
User Interface Modernization
Responsive Web Design: Adopt responsive web design principles to ensure applications are accessible and performant across different devices and screen sizes.
SPA and Frontend Frameworks: Consider building modern single-page applications (SPAs) using frontend frameworks like React, Angular, or Vue.js for improved user experience and interactivity.
DevOps Practices
Automation: Implement continuous integration (CI) and continuous deployment (CD) pipelines to automate testing, builds, and deployments.
Monitoring and Logging: Integrate monitoring and logging tools to track application performance, detect issues, and facilitate troubleshooting.
Data Modernization
Data Migration: Migrate data to modern databases or data lakes to enable advanced analytics, real-time processing, and scalability.
Implement Caching: Introduce caching mechanisms to improve application performance and reduce database load.
Security Enhancements
Identity and Access Management (IAM): Implement modern IAM solutions like OAuth 2.0 or OpenID Connect for secure authentication and authorization.
Data Encryption: Encrypt sensitive data at rest and in transit to protect against data breaches and unauthorized access.
Training and Knowledge Transfer
Invest in Training: Provide training and resources to developers and teams to familiarize them with modern technologies, best practices, and architectural patterns.
Knowledge Sharing: Encourage collaboration and knowledge sharing among team members to foster a culture of continuous learning and improvement.
By following all these steps it is easier and also reliable to transition an old legacy Dotnet application to higher versions of .Net.